
How Signority Secures Your Data
My last blog, Three Stages of Data; In Transit, At Rest, & In Use described each of the three data stages and touched on how each stage requires a different approach to security and privacy. Today we are going to talk about:
- when your data enters each of the three stages during the workflow, and
- how Signority secures your data.

If you’ve used Signority you know that every document has a workflow. The workflow begins at the creation of the document and ends when it’s been stored after it has been signed by all participants.
During the it’s workflow your document and any data related to it, enters all three stages of data at various times. Here is each of the data stages and when your document enters that stage during the workflow.
In Transit: Your information related to your document is in transit (or in motion) when:
- someone registers for a new account
- you send the email notifications to the signers that there is a document ready for signing, and,
- when the document has completed the workflow, meaning it has been signed by everyone, and a copy of the document is sent to each of the document participants (senders and recipients).
At Rest: All information related to the document and the document itself is at rest:
- when it is waiting for the next person in the workflow to sign the document
- it is stored on our servers once the workflow has been completed.
In Use: Your document and any related data, i.e.: the audit trail, are ‘in use’:
- when a recipient or user are editing the document by adding the required information and/or signatures
- the Signority platform is updating the audit trail with any actions, i.e.: signed, id verification, etc.
Signority starts our security process with our employees. All employees and sub-contractors must be security cleared with the federal government security clearance program. And they must complete a minimum amount of security and compliance training each year.
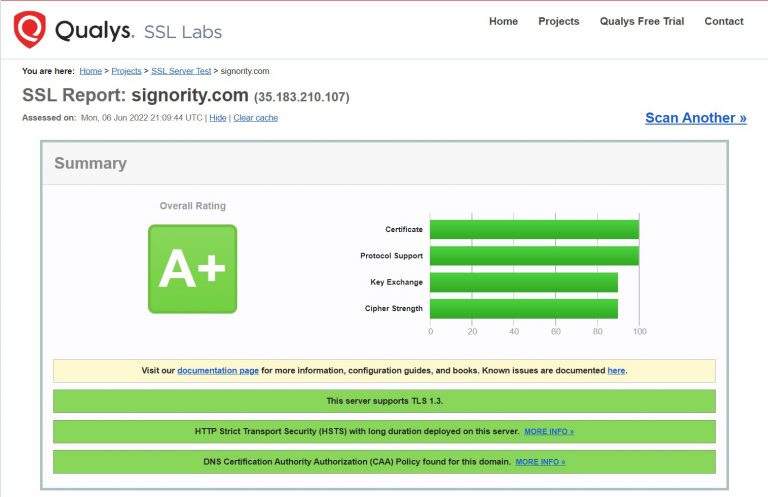
For In Transit and In Use data Signority eSignature Platform services using strongly encrypted extended validation (EV) Transport Layer Security (TLS) certificates to encrypt the data in transit between users and the Signority eSignature Platform. We only allow the highest security TLS 1.2 and 1.3 protocols, and do not allow weaker TLS or SSL. The article linked above explains in detail what EV and TLS certificates are, what they do, and why we use them.
If you would like to know our rating, here is the most current certificate for Signority at the time of this blog post.
We also do not allow the use of older browser versions. Older versions are not updated with the latest security features and updates to ensure a secure browsing connection.
Data at rest data at rest is encrypted by using state-of-the-art AWS encryption technology and we salt usernames & passwords.
What is a ‘salted’ username and password? A salted username and password is a process where they are converted through a ‘hashing algorithm’ into an unintelligible series of numbers and letters. You can read a more detailed breakdown here at Okta.com.
Plus, we offer masked tags for end users to encrypt their sensitive information on documents.
If you are not a technical person, think of it this way:
- Your information is locked in a box that requires a key.
- That key is locked in another box that requires another key to open it.
- And that box, with your box, is in a box that is password protected.
So your data is guarded with multiple layers of protection ensuring your data is secure and private.
If you would like to know more about how Signority protects customers data and privacy I encourage you to go to our Trust Centre. In Signority’s Trust Centre you can review our approach to Security, Privacy, Compliance, and Legislation (Legal).
Have questions?
Contact us by:
- calling at 833-222-1088,
- using the chat icon on the bottom right of your screen,
- or through our contact form.
Look for my next blog, ‘What is Data Residency? And Does it Matter?‘
