
The Three Stages of Data; In Transit, At Rest, In Use
What are the three stages of data and what is the difference?
When evaluating the security of a new software for use within your organization, such as an eSignature software, you may have come across terms like ‘Data at Rest’ and ‘Data in Transit’.
These phrases indicate the stage your data is in and are often used when discussing the protection of data. The approach and methods required to protect your data changes depending on the type of information you are looking to protect and what stage it is in. To learn more about securing your data, read this article on Data Security.
Before you learn how to protect your data you must first understand the three different stages of your data because each stage requires a different approach.
They are: Data in Transit, Data at Rest, and Data in Use.
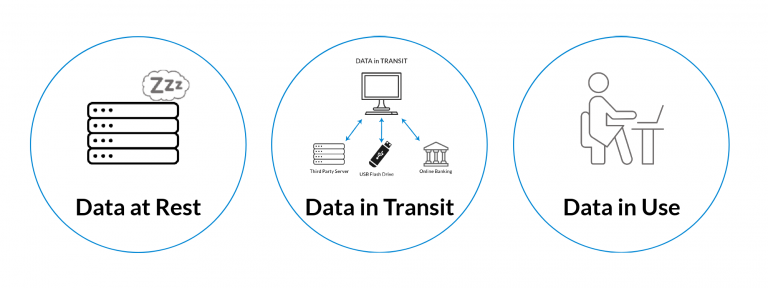
Data in Transit, sometimes referred to as ‘data in motion’, is data that is actively moving from one point, or location, to another. It can be traveling across the internet or through a private network. Data in motion is also data being transferred from a local storage location (hard drive, USB, etc.) to a cloud storage device (Google Drive, OneDrive, Box, etc.).
You create data in transit each time you upload information to a partner organizations site, download the balance of your savings account from your bank online, or save something to a USB flash drive.
Data at Rest is data that is not actively moving from device to device or network to network. This data is usually stored on a hard drive, in the cloud, on a USB, or stored in some other way.
And ‘Data in Use’ is data that is being stored passively in a stable destination, but is being utilized in other parts of the IT architecture. It may be in the process of being created, edited or updated, erased, or accessed through different interface endpoints.
Think of a document you have on our computer that you update, edit, or delete. Any of those actions create the instance of the document and its data being ‘in use’.
There is also one other aspect to data that will be talked about, Data Residency. Data Residency deals with where your data is stored. When we talk about where your data is stored we are not speaking about the kind of device or drive it is on but where is it located in the world.
Data Residency is a key factor in many data laws or regulatory requirements imposed on data that govern a country or region in which it resides. These laws address key requirements in data protection and privacy. When evaluating a software look for their Trust Centre, this is where they will explain how they protect your data and privacy.
Protecting sensitive data is a high priority for any organization. And, as previously mentioned, the approach and methods required to protect your data changes depending on the type of information you are looking to protect and what stage it is in.
Data at rest is often considered to be less vulnerable than data in motion, but hackers and nefarious individuals often prefer data at rest and find it a more valuable target than data in transit.
We will review some of the methods used to protect data in each stage in an upcoming blog.

